Kz43x9nnjm65, It started, as these things often do, with a simple, mundane task. I was on the phone with my internet provider, locked in the classic ritual of modern life: attempting to dispute a mysterious charge on my bill.
“I’m sorry, sir,” the customer service representative said, her voice a practiced blend of empathy and steel. “I can’t process the credit without the transaction ID from your original payment.”
No problem. I’m an organized person. I opened my email, clicked on the search bar, and typed the date of the payment. A dozen emails popped up. None were from my ISP. I tried searching for “payment confirmation,” “bill,” and the amount. Nothing.
Frustration began its slow, familiar creep. I knew I’d paid it. I remembered the moment. I’d been drinking coffee. The sun was coming through the window. But the digital proof, the artifact of that moment, was gone. Vanished into the ether.
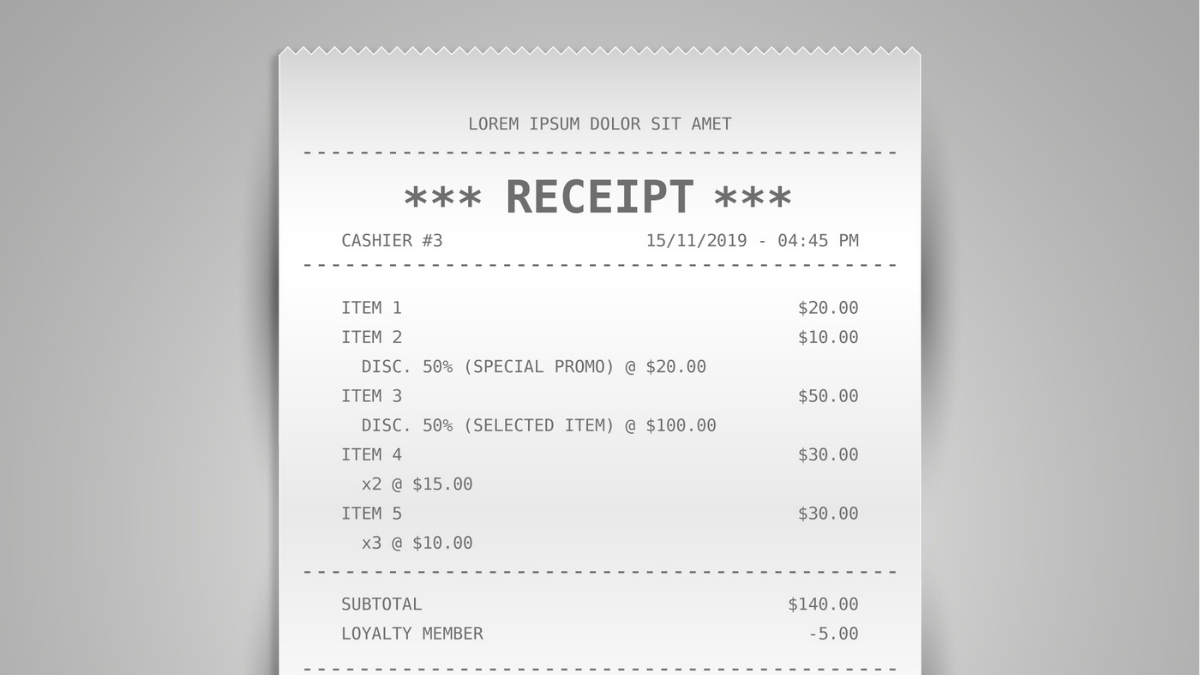
Then I saw it. A single email from months ago, its subject line a cryptic jumble of characters: kz43x9nnjm65.
It looked like spam. It looked like a error code. It looked, for all the world, like digital static. But something made me click on it. And there it was. Not a friendly “Thanks for your payment!” message with my name in a cheerful font, but a stark, automated receipt. Transaction ID: kz43x9nnjm65. Amount: $89.99. Status: Completed.
This meaningless string of letters and numbers—this kz43x9nnjm65—was the only thing standing between me and a $90 credit. It was the key. It was the proof. It was the stand-in for a handshake, for a paper receipt, for a promise kept.
And it got me thinking. How many of these digital ghosts are we surrounded by? How many kz43x9nnjm65s are floating in the cloud, holding our modern lives together?
The Alchemy of the Unseen: How a String of Characters Builds Our World
We live in an age of abstraction. Our wealth is not gold in a vault but numbers on a screen. Our friendships are not just conversations on a porch but collections of likes and comments. Our agreements are not signed parchment but “I Agree” buttons clicked in haste.
And our proof—the evidence of our actions, our purchases, our existence within these systems—is often a string of characters like kz43x9nnjm65.
This isn’t just a random receipt code. It’s a perfect metaphor for the invisible architecture of our digital lives. Let’s break down what a code like this truly represents.
1. It is a Unique Digital Fingerprint.
In the vast, endless database of my internet provider, there are millions of transactions. The system cannot identify my $89.99 payment by my name or the date alone. Those are common data points. It needs a primary key—a unique identifier that points to one, and only one, specific record. kz43x9nnjm65 is that key. It is a guarantee of uniqueness in a sea of data. It is my transaction’s name in a language only the machines understand.
2. It is a Token of Trust.
That string of characters is a token of completion. It tells a story: a request was made, a payment processor was engaged, funds were verified, a confirmation was sent. kz43x9nnjm65 is the culmination of that chain of trust. It’s the digital equivalent of a “Paid in Full” stamp. It’s a contract, condensed into 11 characters.
3. It is a Bridge Between Worlds.
When I read that code out to the customer service agent—“K-Z-4-3-X-9-N-N-J-M-6-5”—I am performing a ritual. I am speaking the language of the machine to a human being. She then inputs that code into her terminal, translating it back into the data it represents. This code is a bridge. It allows a human problem (“I was overcharged”) to be solved by interfacing with an inhumanly vast digital system. We are all, constantly, speaking machine language to get what we need.
The Anxiety of the Ephemeral: When the Ghosts Disappear
My story had a happy ending. I found the code. I got the credit. But the frantic search, the momentary panic, the feeling of helplessness—that was real. It highlights a deep, modern anxiety.
What if I hadn’t found it? What if I’d deleted the email? What if their system had a glitch and the record of kz43x9nnjm65 simply vanished?
We have outsourced our memory to machines. We trust corporations, platforms, and cloud services to be the archivists of our lives. Our photos are on Instagram. Our documents are in Google Drive. Our proof of purchase is in an email inbox with a laughably small search function.
A code like kz43x9nnjm65 has immense power, but it is also incredibly fragile. It has no physical form. It can be deleted with a click. It can be lost in a crashed server. It can be rendered useless if the company that issued it goes out of business or simply changes its software.
This creates a low-grade, constant hum of vulnerability. Our identities, our finances, and our histories are often reduced to these fragile digital tokens. We are all one forgotten password, one server outage, one accidental deletion away from a piece of our story becoming inaccessible.
Humanizing the Machine: The Stories Behind the Codes
The trick to navigating this world isn’t to become a paranoid backup enthusiast (though backing up your data is a very good idea). It’s to re-humanize these systems. It’s to remember that behind every cold, alien string of characters, there is a human story.
kz43x9nnjm65 wasn’t just a code to me. It was:
-
The relief of knowing my internet wouldn’t be shut off.
-
The 45 minutes I spent on my budget that Sunday afternoon.
-
The coffee I was drinking when I clicked “Submit Payment.”
-
The frustration of the dispute and the victory of it being resolved.
Every tracking number, every order confirmation, every license key, every booking reference—they are all chapters in our biographies. They are the digital scars and souvenirs of our journey through the 21st century.
-
GH78P2T91L is the birthday gift for your nephew that arrived just in time.
-
22BXK89L3 is the plane ticket that took you home for the holidays after two years away.
-
N331J8MK45 is the software that helped you build your first website.
These codes are the sterile, machine-generated titles for deeply human experiences of anticipation, joy, relief, and accomplishment.
Finding Our Way in a Coded World: A Practical Philosophy
So how do we live well in a world run by kz43x9nnjm65? We develop a new kind of literacy.
-
Embrace the Ritual of Documentation: When something important happens digitally—a big purchase, a contract, a booking—document the documentation. Take a screenshot. Save the PDF. Print it out and throw it in a drawer if you have to. Create a “Digital Receipts” folder in your email. You are not just saving a code; you are saving a key to a memory and a tool for your future self.
-
Understand the Power of the Key: When you see a code like this, don’t just dismiss it as junk. Recognize it for what it is: a key. Highlight it. Copy it. Paste it into a note. That string is power. It is your leverage and your proof. Treat it with the same respect you would a physical key to your house.
-
Tell the Story: When you’re on the phone with customer service, don’t just read the code. Frame it. “Hi, I have a transaction here, ID kz43x9nnjm65, from April 14th for $89.99. I believe I was double-charged.” You are providing the data and the narrative. You are helping the human on the other end connect the machine’s language to a human problem.
The string kz43x9nnjm65 is a tiny, mundane miracle. It is a pact between human and machine. It is a whisper of order in the chaos of data. It is a digital ghost that holds very real power.
The next time you see one—in your inbox, on a screen, in a confirmation message—pause for a second. Don’t just see a random jumble of characters. See a story. See a key. See a tiny, indispensable cog in the invisible machine that makes our modern world turn. It’s the proof that in the digital age, even the most human of experiences—like keeping the lights on—can come down to a language of our own creation.